Alternatives to Notebook PEAs of Peafactory
Actually you can use each file encryption program to encrypt text files, but there is one advantage of
editors using encryption: The plaintext must never be stored on the disk.
Self-decrypting archives or browser-based editors can hold the plaintext in memory and display
it without storing unencrypted data.
The advantage of the Notebook PEA compared to other programs is mainly the platform independence and the more robust key derivation functions. But perhaps other properties are more important for you. Here is a list of other programs to display and encrypt texts.
I will introduce only open source programs. This is not only because I don't want to make any advertisements for commercial products, but also due to the fact that closed source security software is not very trustworthy. There is no chance to check for bugs, backdoors, weak cryptography...
NPPCrypt
NPPCrypt is a plugin for the editor Notepad++ for Windows, which allows the encryption of data using a password.
It is a bit hard to find informations about NPPCrypt. But at least I found the
source code.
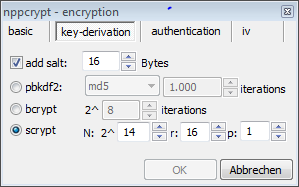
NPPCrypt uses ciphers and other stuff from openSSL. There are many ciphers, modes and hash functions to choose from.
And NPPCrypt also offers Bcrypt and Scrypt along with PBKDF2 as key derivation functions... Wow!
Notepad ++ is undoubtedly the editor with the most features here and NPPCrypt seems to be the
encryption tool with the best cryptographic options.
Scrypt is offered with the default parameters of the scrypt paper from 2010 (N=2^14, r=8, p=1). The
r-parameter should be increased now, but this can be done in the setting. The default parameter for Bcrypt is 8 (2^8 iterations)
- the recommendation is from 1999... This should be increased too, but this can be also done in the setting.
There are some minor drawbacks. I can't see any reason to offer weak ciphers like DES or RC2 and a weak mode of
operation like ECB. Authenticated modes refer only to AES as cipher. And of course: Notepad++ is Windows-only...
Besides these little objections NPPCrypt was a very positive surprise.
CryptoTE
Main Page: CryptoTE
Source code: GitHub

For Windows and Linux, there are also repos for Debian, openSuse, Fedora, Gentoo and Ubuntu.
CryptoTE uses Serpent (256 keybits) in CBC mode for encryption. Key derivation is done by PBKDF2 with HMAC(SHA256).
I haven't found the number of iterations, it might be 1000, but there is no possibility to increase it.
CryptoTE uses Botan-1.6.4. as crypto library. Botan also offers authenticated encryption modes like EAX, which I would prefer
over CBC mode, and the password hashing scheme Bcrypt, which I would prefer over PBKDF2.
Clear and handy program with many features.
This is the best documented and supported program here.
Laverna
Laverna is a web app written in JavaScript. The data are stored only on client-side.
Because Laverna runs in a browser, it is not platform dependent.
There is a homepage of the project and the source can be found
at GitHub.
 Image from static-laverna download
Image from static-laverna download
Laverna uses the SJCL library with PBKDF2 (n the new version 10000 iterations as default) to derive the key
and AES in an authenticated-encryption mode. Parameters like the number of iterations can be
modified in Laverna.
Of cource, Scrypt or even Bcrypt would be a better choice than PBKDF2.
Using JavaScript in a browser to store notes might a bit questionable, because this increases the number of possible attacks,
especially side channel attacks, but besides this objection, the program seems to be good choice.
At their GitHub site the authors announce to consider Laverna like an open source alternative to Evernote. In terms
of security Laverna seems to me much better than the commercial Evernote, which has performed the encryption
before 2014 with the weak RC2 (now it uses for new notes AES in CBC mode without any authentication).
Joplin
 Image from Joplin homepage
Image from Joplin homepage
Joplin is an open source note taking application for many platforms: Windows, Linux, macOS, Android, iOS and FreeBSD. End-To-End Encryption is not enabled by default, but must be enabled manually (Joplins E2EE). Joplins encryption uses the default settings from Stanford Javascript Crypto Library (PBKDF2 with 1000 iteration, optionally 10000, AES in CCM mode) and an additional encryption of the master key with 101 iterations (see: encryption source code). The security is similar to Laverna: authenticated encryption, at least a key derivation function, but not a memory-hard one. Homepage: Joplin, Source code: Joplin on GitHub.
PryNotes
Home: prynotes.com
Source code: GitHub
PryNotes is a web based note application. The data can be accessed via the web.
PryNotes bases on AES in CBC mode using the Keyczar toolkit. The key derivation is performed by repeatedly hashing
the password hash along with a salt (1000 iterations). This is not a standardized key derivation function, but better
than just hashing the password.
def secret_encrypt(phrase, text, base64=False):
try:
text = text.encode('utf8', errors='ignore')
except:
pass
salt = os.urandom(SALT_LENGTH)
iv = os.urandom(BLOCK_SIZE)
paddingLength = 16 - (len(text) % 16)
paddedPlaintext = text+chr(paddingLength)*paddingLength
derivedKey = phrase.encode('utf8', errors='ignore')
for i in range(0,DERIVATION_ROUNDS):
derivedKey = hashlib.sha256(derivedKey+salt).digest()
derivedKey = derivedKey[:KEY_SIZE]
cipherSpec = AES.new(derivedKey, MODE, iv)
ciphertext = cipherSpec.encrypt(paddedPlaintext)
ciphertext = ciphertext + iv + salt
if base64:
return base64.b64encode(ciphertext)
else:
return encrypt_it(ciphertext.encode("hex"))
SafePad
SafePad is an encrypted editor written in C# for Windows.
SafePad includes a nice password generator, an onscreen keyboard to avoid keyloggers and a
password strength meter to indicate the strength of a password.

Bcrypt is used as key derivation function (since version 1.2 ) and AES as cipher.
A single password is pre-hashed with SHA-256, then hashed
with Bcrypt. This is an commonly used combination since Bcrypt limits the password length.
Two (non-serious) objections:
As far as I can see, the number of Bcrypt rounds is the recommanded value of 1999, which should
be increased and AES is used in CBC mode that does not provide integrity.
You can use optionally two passwords.
Two passwords are concatenated and hashed with Bcrypt. Although I see no advantage against the use of passphrases
consisting of two words, this is not a security objection.
Downloads, source code and more informations can be found at SafePad on CodePlex
CrocodileNote
There is a Windows client since 2014 (beta stage) for the Android app CrocodileNote.
CrocodileNote uses AES-256 for encryption and PBKDF2 as key derivation function.
Download can be found at Groomiac News,
source code at GitHub.
Applications with simple hash instead of a key derivation function
LockNote
Steganos LockNote is a "self-modifying encrypted notepad" for Windows.
The source code can be found at Sourceforge .
Unfortunately, the linked homepage contains only references to commercial products, instead of information about LockNotes.
But there is also the locknote site of Steganos,
which announces:
Hide your serial numbers, passwords, phone numbers and everyday notes in a safe place. Your informations will be encrypted using a password and most modern AES 256bit encryption technology."
LockNote is widely used (Steganos states 452.479 downloads), has existed for many years (since 2006) and some computer
magazines recommends it.
The last version 1.0.5 is from 2010, when I checked, it was released one month before.
LockNote is relatively small, the exe file is only 401,4 KiB.
LockNote is approved, reliable software, but it's major drawback is the weakness of the underlying cryptography.
It uses AES in CFB mode for encryption; a SHA-HMAC over cipher text is appended to encrypted messages to provide the
integrity of the data. There might be better options, but I think this is o.k.
The problem is: LockNote does not use any key derivation function, neither PBKDF2 nor any other. It uses just a
simple SHA256 to derive the key from the password.
SecByteBlock key(SHA256::DIGESTSIZE);
SHA256().CalculateDigest(key.begin(), passphrase.begin(), passphrase.size());
SecByteBlock iv(IV_SIZE);
AESPHM_GenerateIvFromSeed(ivSeed, iv.begin());
CFB_Mode<AES>::Encryption encryptor(key.begin(), key.size(), iv.begin());
// Encrypt padding and payload
encryptor.ProcessString(output, paddingLen);
encryptor.ProcessString(payload, input.begin(), input.size());
// Calculate MAC
HMAC<SHA>(key.begin(), key.size()).CalculateDigest(digest, output, digest-output);
This is not comprehensible, because the used library Crypto++ contains at least some password based key derivation functions
like PBKDF1 und PBKDF2, although there is no Bcrypt or Scrypt. The renunciation of any key derivation function
makes it easy to perform dictionary attacks using any custom hardware like GPUs.
It is also used no salt, so even rainbow tables can be used to speed up the cracking.
Encrypted Notepad
Encrypted Notepad Web Site
Simple Java text editor for desktop and Android.
Encrypted Notepad uses AES in CBC mode to encrypt the text and SHA1 to derive the key.
fSecrit
fSekrit is still Freeware and not Open Source, but the author claims, it maybe one day open. There is still no possibility to have a look inside the code, but the readme file explains, fSekrit uses AES in CBC mode for encryption and SHA256 to derive the key. So, it seems quite the same problem as for LockNote.